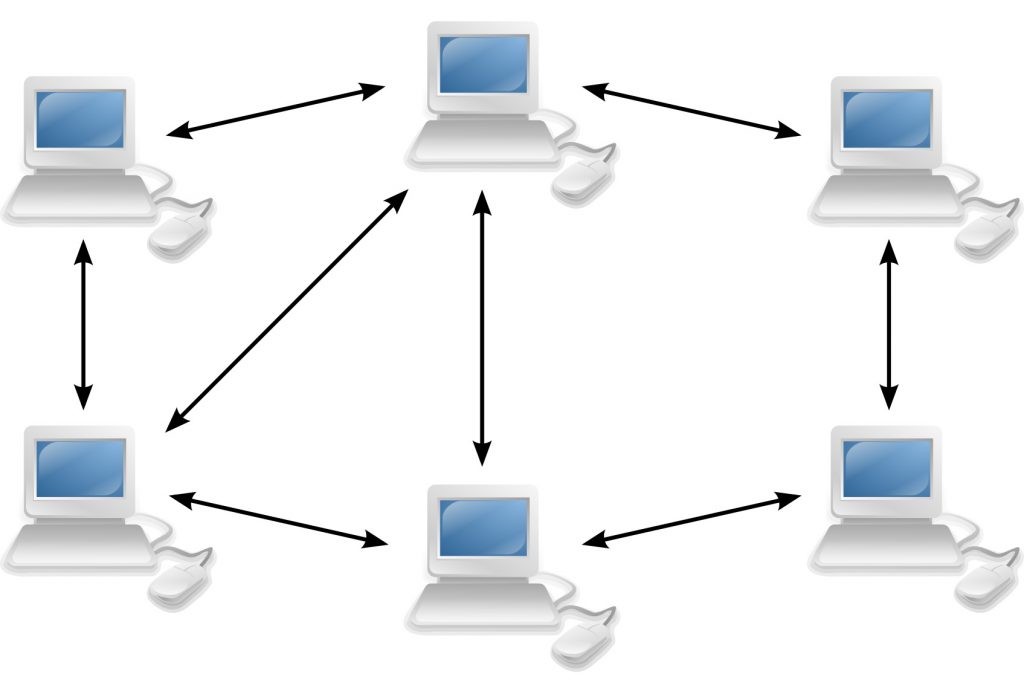
In the world of networking there is such a thing as the term peer to peer. Maybe some of us are still not familiar with the term. Basically peer to peer is a computer network consisting of several computers in a network that communicate with each other.
Before reading further, for those of you who want to know more about Netdata, you can contact us directly via the link below.
Consultation Via WhatsappIn a p2p network to communicate with each other does not require a hub or switch. P2p only requires 1 piece of UTP cable to connect between the two computers. The most important thing in a peer to peer network is service and resource sharing. However, this network is not recommended for needs with larger networks. Why and what is peer to peer and what are the advantages? Let’s look at the following explanation.
Table of Contents
Peer to Peer Explanation
Peer to peer is a computer network in which each computer is connected to each other on the network, both server computers and client computers. Each computer has the same position, there is no central control or server on a special assignment.
Data exchange occurs between computers either directly, there is no need to regulate the distribution of access rights. On the security side, every computer user has full responsibility for each of his own computer devices.
For example, computer A on a p2p network wants to retrieve data on computer B. Computer A will act as a server so that it can access data on computer B. Computer B will act as a client. This applies vice versa if computer B wants to retrieve data from computer A, computer B will act as a server, while computer A will act as a client.
History of Peer to Peer Networks
The beginning of the peer to peer network concept began in the 1980s. However, this new network popular
The concept of peer to peer networks actually existed from the 1980s. However, this new network popular
by Microsoft while determining the OS for Workgroups. in th. similar releases later included a distributed application called usenet. This application was created by Tom Truscott with his partner Jim Ellis so that it can serve users by using newsgroups.
At that time, internet facilities that could quickly exchange information were not widely known. Generally, the process used to carry out the exchange of information is a batch file. The next file is a file whose contents are data that is being processed or will be transmitted from beginning to end.
The best time to exchange information using p2p is during the night. This time is the best time for big countries because the DLD line is currently empty of users. So, the function of this application is not able to be distributed.
Then, the first generation of per to per applications emerged, namely FidoNet. This application was quite successful and achieved a great level of popularity. The application created by Tom Jennings was released in th. 1984 to exchange messages between users of the Bulletin Board System or BBS which are certainly very diverse. So, FidoNet is arguably another originator of p2p applications.
Over time, more precisely in th. In the 90’s, applications developed that raced with the concept of p2p. Examples are Kazaa, BitTorrent, eDonkey, etc. This p2p application can not only be used by home users, but can also be used by companies.
In addition, while this includes a peer to peer lending network related to the financial world. Many startup companies in the field of credit and money are participating in and also using p2p networks. This system is expected to be able to make it easier for people to make money loans.
Peer To Peer Network Characteristics
This network has several special characteristics used by Microsoft by releasing the Windows operating system for groups. There are several characteristics used by the network, among others:
When using this system, you don’t need a hub anymore. Why? because the computer is connected to each other with a UTP cable. The connected computer also does not require the same specifications. All you have to do is add the network card directly to the computer so that it can be connected together.
Do not have a computer that functions as a dedicated server.
As previously said, peer to peer does not use a client server system, meaning there is no control center to connect to each other.
Each computer on the network is both a server and a client.
Even though there is no client server system, Peer To Peer can change each computer to serve as a server when it wants to provide data, while other computers can serve as clients.
There is no control on network security settings
With no control for network security settings, making Per To Per easy to configure but has a weakness for weak network security because each connected device can fully access the data on each device.
Does not require equivalent computer specifications to be connected in one network
To connect between computers that have different specifications, you can easily implement this network.
Advantages of Using a Peer To Peer Network
- No need to buy additional server software or hardware.
- Easy and cheap configuration and no need to use an admin to manage this network.
- If a server dies, it will not affect the rest of the network.
Disadvantages of Using Peer To Peer Networks
- If an error or damage occurs, it is not easy to fix because you have to check every computer on the network to find the location of the damage.
- The way of working is lower than a network with a client server because each computer will manage each job and its own application.
- Each user must set their own security on existing network services.
Peer to Peer Network Working Principles
This network works by connecting two or more computers in a network. Each computer in this topology acts as a server and client.
For equipment, it can share the resources of all computers on the same network. In the process, no single computer has the highest access priority or the highest responsibility for sharing resources. Everyone has the same position.
To create this network, you don’t have to use a hub or switch, but you just need to use a twisted pair cable that attaches to the network card of each computer.
Usually, this network only requires two computers that have a network card and are open to the same network. After the computer is connected, users can share data and information with other users directly and purposefully.
NetData is a company that provides technology-based services with the best service and quality, if you are interested in us you can contact us directly via this link or via our contact form here.
![]()