Secure Shell / Socket Shell (SSH) – Remote work is indeed very reliable. Because like this, if you have a device that is far from the user, even continents apart, you can do it by utilizing a technology called SSH. SSH is very possible for you to do remote servers or other devices that are connected to the internet network. However, what exactly is SSH?
Before reading further, for those of you who want to know more about Netdata, you can contact us directly via the link below.
SSH will be discussed in this article from understanding, how it works, to the function of SSH itself that you need to know.
Table of Contents
SSH Explanation
SSH, also known as Secure Shell or Secure Socket Shell, is a network protocol that provides users, especially system administrators, a secure way to access computers over an insecure network.
SSH also refers to a suite of utilities that implement the SSH protocol. Secure Shell provides strong password authentication and public key authentication, as well as encrypted data communication between two computers connected over an open network, such as the internet.
In addition to providing strong encryption, SSH is widely used by network administrators to remotely manage systems and applications, allowing them to log into other computers over a network, execute commands, and move files from one computer to another.
History of SSH
This SSH was first created in 1995. The person who invented it was Tatu Ylönen who is Finnish, in response to a password tracker attack on his university. Seeing the flaws in plain text communication for secure information, Tatu created Secure Shell/SSH with a strong emphasis on encryption and security.
This version of SSH was developed for several years as freeware with a liberal license, but as its SSH Communications Security Corporation started limiting licenses and commercializing SSH, alternative forks became popular. The most popular fork, OSSH, by Swedish programmer Bjoern Groenvall, was chosen as a starting point by several developers of the OpenBSD project.
SSH Encryption Types
As explained above, SSH is an encryption for remote network security. This encryption consists of various types, each of which has a different meaning.
What are the types of SSH?
Symmetric Encryption
The first encryption is symmetric. This symmetric encryption can also carry out tasks permanently during the SSH client and server connection process according to the approved method.
The communication method agreement has an object to be able to prevent third parties from reading the data. The Key Exchange Algorithm itself has a role in the process of creating symmetric encryption in the data exchange process.
Not only that, as long as in the process of exchanging this knowledge the keys available on the server or those available on the client are not involved in the exchange so that the algorithm is always safe.
So in a Key Exchange Algorithm this is unique in that the process of data decryption and data encryption can take place on each device either from the server or client.
Asymmetric Encryption
Next is asymmetrical. This is very different from symmetric encryption. If symmetric encryption only uses one key, asymmetric encryption will have two keys, namely a private key and a public key.
For private keys, this will generally only be owned by the server and for public keys or public keys, this will be owned by the client or user. As the name implies, the public key can openly be used by clients.
However, when in the process of exchanging data, the encryption process can only be done by the private key and the public key and cannot be shared with a different key model.
So the connection that can take place is a one-way connection which results in hosts like this client or server who have a public key forever unable to open their messages even though they are encrypted.
This is what causes third parties to try to steal and or peek when data exchange is in progress and cannot read it.
Hashing
SSH uses an encryption technique called hashing encryption. This hashing is one of the wrong types of cryptography which apparently cannot be decrypted so it is named one way hash or one way hashing.
This one-way hashing or one-way hash has the benefit of causing a long encryption that has no pattern of understanding to be exploited. So, for the benefit of one way hash encryption this is to produce a value that is unique and includes length.
This encryption can certainly secure every data while part of the exchange process is in progress during this SSH connection.
Starting from this hashing encryption, all data will experience one-way encryption and cannot be reversed or decrypted.
One-way hash or one-way hashing cannot be used for all styles originating from data exchange. SSH can only use one-way encryption or one-way hash to be able to check the authenticity of a message and the like.
Get to Know the Basic Features of SSH (Secure Shell)
In the realm of SSH, there are various basic features, starting from SSHd, RFC, tunneling and port forwarding, and the last one is X11.
What are the explanations for each of these features?
SSHD
The Secure Shell Daemon application (SSH daemon or sshd) is a daemon program for ssh. This program is an alternative to rlogin and rsh and provides encrypted communication between two untrusted hosts over an unsecured network. Sshd is a daemon that listens for connections from clients on port 22.
RFCs
RFC (short for Request For Comments) is a document that describes Internet and TCP/IP standards, protocols, and technologies. Since 1969, approximately 2400 Requests for Comments (RFCs) have been published on various network protocols, procedures, applications, and concepts.
Port Tunneling and Forwarding
SSH tunneling, or SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. SSH tunneling allows connections made to a local port (that is, to a port on your own desktop) to be forwarded to a remote machine over a secure channel.
X11
This is a feature of SSH in this type of forwarding. X11-Forwarding is a secure shell feature, which allows to forward/forward X11 connections through existing SSH shell sessions. This is used to run X11 programs on the server while the ssh-client displays a graphical window through the user’s X11 server.
Benefits of SSH
There are many benefits of SSH, starting from a clear security perspective and there are many more. This benefit can be felt when using SSH with good quality.
SSH has benefits including:
Control Data Remotely & Securely
Present in all data centers, SSH is shipped by default with every Unix, Linux, and Mac server. SSH connections have been used to secure many types of communications between local machines and remote hosts, including secure remote access to resources, remote command execution, delivery of software patches, and updates and other administrative or management tasks.
Avoiding Cyber Attacks
As with the history of SSH, the benefit that can be obtained from using it is avoiding cyber attacks. SSH will be able to encrypt running data so as to minimize the occurrence of cyber attacks.
DNS and IP spoofing
Explaining IP spoofing will be very easy if you look at the flow as below:
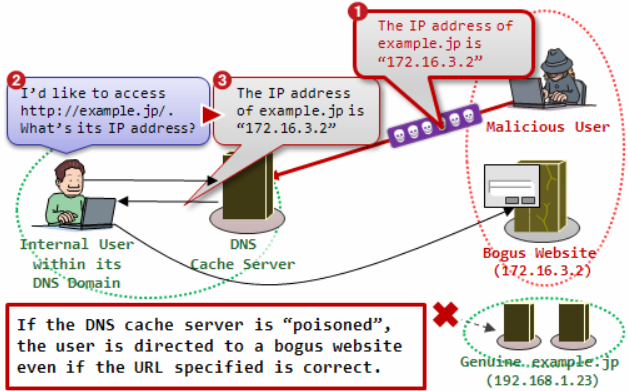
Through DNS spoofing, hackers can do deflections that direct the victim’s PC to a fake website (see the DNS Spoofing illustration above). This deflection is very easy to do, considering that the DNS protocol does not have any security mechanism. This can be prevented by using a good firewall application. In the latest firewall applications, usually the DNS cache is stored neatly, so if we have visited the web before then DNS Spoofing can be prevented.
Strengthening Security
SSH can strengthen security. SSH provides password or public key based authentication and encrypts the connection between two network endpoints. It is a secure alternative to older login protocols (such as telnet, rlogin) and insecure file transfer methods (such as FTP).
How SSH Works
If you want to understand how SSH works, it is to take advantage of the client-server model to allow authentication of two remote systems and encryption of data passing between them.
SSH operates on TCP port 22 by default (although the SSH port can be changed if needed). The host (server) listens on port 22 (or another SSH-defined port) for incoming connections. It sets up a secure connection by authenticating the client and opening the correct shell environment if verification is successful.

The client must initiate an SSH connection by initiating a TCP handshake with the server, ensuring a secure symmetrical connection, verifying that the identity provided by the server matches previous records and providing the required user credentials to authenticate the connection.
There are two stages to establishing a connection first, both systems must agree on encryption standards to protect future communications, and second, users must authenticate themselves. If the credentials match, then the user is granted access.
NetData is a company that provides technology-based services with the best service and quality, if you are interested in us you can contact us directly via this link or via our contact form here.
![]()


