Security is one of the most important things in any case. No exception for data security, in IT itself there is its own science that discusses security, namely cryptography.
Before reading further, for those of you who want to know more about Netdata, you can contact us directly via the link below.
Consult via WhatsAppMaybe what many people know is technology and information security, just by entering a username and password. Yet behind it there is something more complicated.
Table of Contents
What is meant by Cryptography
Cryptography is a method of protecting information and communications through the use of codes, so that only those intended to read and process them can.
In computer science, cryptography refers to secure information and communication techniques derived from mathematical concepts and a set of rule-based computations called algorithms, to modify messages in ways that are difficult to decipher.
These deterministic algorithms are used for cryptographic key generation, digital signing, verification to protect data privacy, web surfing on the internet and confidential communications such as credit card and email transactions.
History of Cryptography
The word cryptography comes from the Greek “kryptos” which means hidden. The origins of cryptography usually date back to around 2000 BC, with Egyptian hieroglyphic practices. It consists of complex pictograms, whose full meaning is known only to an elite few.
The first known use of modern ciphers was by Julius Caesar (100 BC to 44 BC), who distrusted his emissaries when communicating with his governors and officers. For this reason, he created a system in which each character in his message was replaced by a character three positions in front of him in the Roman alphabet.
In recent times, cryptography has turned into a battleground for some of the world’s best mathematicians and computer scientists. The ability to securely store and transfer sensitive information has proven to be a critical factor in success in war and business.
Based on this history, today it can be distinguished if cryptography can consist of two types, namely classical and modern cryptography.
Classic Cryptography
Classic cryptography is done with pen and paper and maybe on a good day keeping your secrets safe from your little sister.
Transitional crypto uses electro-mechanical devices and drives computer development. Classical cryptography in computational terms is at risk of being vulnerable to quantum cryptanalysis.
Modern Cryptography
Modern cryptocurrencies are carried out on computers and guarding chats from communication platforms guarantees safety from eavesdropping.
Asymmetric crypto development allows you to have secure online communication with someone you have never met. Modern cryptography is the less risky of quantum cryptanalysis.
How Cryptography Works
Basically, this cryptography can be understood very easily. The way it works is fairly easy, but for its implementation so that it is very difficult to solve, it is very important for how this cryptography works.

If you look, there is such a thing as an encryption and decryption process. Cryptography is closely related to the disciplines of cryptology and cryptanalysis. This includes techniques such as microdots, combining words with pictures and other ways to hide information in storage or transit.
However, in today’s computer-centric world, cryptography is most often associated with scrambling plaintext (plain text, sometimes referred to as cleartext) into ciphertext and then back again.
Encryption
This is a method in which information is converted into a secret code that hides the true meaning of the information. The science of encrypting and decrypting information is called cryptography.
In the computer world, unencrypted data is also known as plaintext, and encrypted data is known as ciphertext. The formula used to encode and decode messages is called an encryption algorithm, or cipher.
Decryption
The conversion of encrypted data into its original form is called Decryption. This is generally a reverse encryption process. It decodes encrypted information so only authorized users can decrypt data as decryption requires a secret key or password.
To be able to carry out this decryption process, a key is needed that can change the encrypted text back to how it was before it was encrypted.
Key
The encryption key is usually a random string of bits specially created for scrambling and scrambling data. Encryption keys are generated by algorithms designed to ensure that each key is unique and unpredictable. The longer the key is created this way, the harder it is to decode the encryption.
Algorithms in Cryptography and the Advantages of Each
In the world of cryptography, the algorithm can be divided into two things, this difference is a difference that is closely related to past and present usage. There is indeed a development.
The two types are symmetric and asymmetric algorithms.
Asymmetric and symmetric encryption both work in the same way. They make use of shared keys to encrypt and decrypt information. The idea is that when everyone involved knows the same key, they can safely pass information back and forth through this common channel.
Symmetric Encryption

The symmetric encryption method, as the name implies, uses a single cryptographic key to encrypt and decrypt data. It sounds very simple, and it really is. Because this type is already not very useful for now.
DES (Data Encryption Standard)
DES uses a 56-bit encryption key, and is based on the Feistel Structure devised by a cryptographer named Horst Feistel. The DES encryption algorithm is also included in TLS (Transport Layer Security) versions 1.0 and 1.1
3DES (Triple Data Encryption Algorithm)
Very true to its name, is an upgraded version of the DES algorithm that has been released. 3DES was developed to overcome the weaknesses of the DES algorithm and felt used in the late 1990s. To do so, it applies the DES algorithm three times for each data block.
Therefore, 3DES is more difficult to crack than its predecessor DES. It is also the encryption algorithm that is widely used in payment systems, standards and technology in the financial industry.
AES (Advanced Encryption System)
AES works on substitution and permutation methods. First, the plaintext data is converted into blocks, after which encryption is applied using the encryption key. The encryption process consists of various sub-processes such as sub bytes, row shifts, mixed columns, and adding round keys. Depending on the size of the key, 10, 12, or 14 turns should be done.
Asymmetric Encryption
In an asymmetric encryption system, each person has a pair of keys that work together: a public key and a private key. The public key is shared openly with everyone, while the private key must forever be known only to its owner.
This works similarly to a real world lock which has a front door and a back door steplessly opening one without having access to the other.
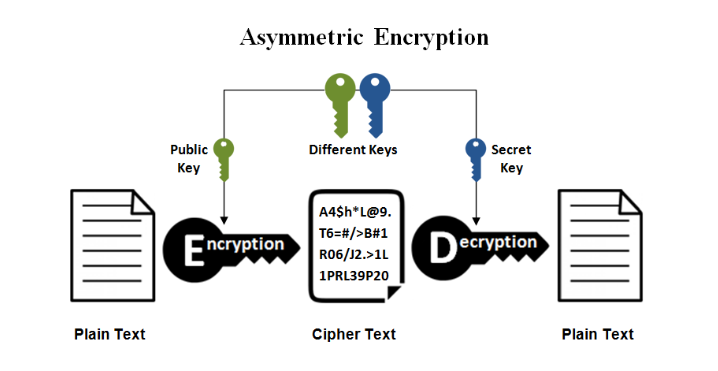
Asymmetric encryption can be divided into two, namely RSA and ECC.
RSA
This algorithm was created by Ron Rivest, Adi Shamir, and Leonard Adleman, hence the name RSA in 1977. And this is a cryptographic algorithm that is still used today. Why can it be used until now? Even though it has been decades adrift and technology and knowledge continue to develop.
So this method involves two very large random perfect numbers, and these numbers are multiplied to produce another large number. The puzzle here is to choose the original perfect number from these gigantic multiplication numbers.
It turns out that this puzzle is nearly impossible—if you use the right key length generated with enough entropy—for today’s supercomputers, let alone humans. In 2010, a group of researchers did research, and it took them more than 1,500 years of computational time (distributed across hundreds of computers) to crack a 768-bit RSA key–which is far below the standard 2048-bit RSA key used today.
ECC (Elliptic Curve Cryptography)
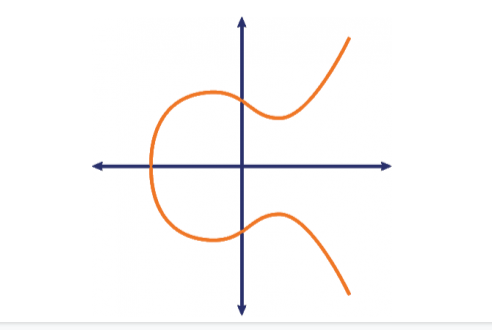
Next up in asymmetric encryption is ECC. In the ECC encryption process, the elliptic curve represents the set of points that satisfy the mathematical equation (y 2 = x 3 + ax + b).
Like RSA, ECC also works on the principle of irreversibility. In simpler words, it’s easy to calculate it in one direction but too hard to reverse it and arrive at the original point. In ECC, the number representing the point on the curve is multiplied by another number and adding another point on the curve.
Cryptographic Example
Actually, in today’s world there are lots of cryptographic concepts that are indirectly used and even unconsciously used every day.
- Digital Authentication/Signature
- Time Stamping
- Electronic Money
- Secure Network Communication
- Anonymous Remailers
- Disk Encryption
Use of Cryptography in Security
Cryptography plays a very important role in information system security. If you say, one of them is how to access a computer network. Usually, there is something that must be verified, such as entering a user and password. This user and password includes cryptography. So, if someone wants to break into the computer network, the data collection about users who can access it will be encrypted while the hacker does not have the key.
NetData is a company that provides technology-based services with the best service and quality, if you are interested in us you can contact us directly via this link or via our contact form here.
![]()


