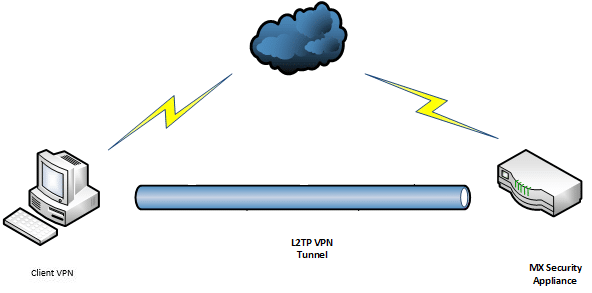
VPN Tunnel – Maybe all of you have known or even used this feature called VPN. Yes, in general, VPNs are very helpful in accessing the internet, but by taking advantage of extra security for your network. VPN tunnel can also be the same definition of VPN.
Private properties in VPN are obtained because the connection made is usually encrypted so it is safe from eavesdropping.
Table of Contents
Explanation About VPN Tunnel
A VPN tunnel is an encrypted link between your computer or mobile device and an outside network.
It is short for virtual private network tunnel can provide a way to cloak some of your online activities.
How? A VPN tunnel connects your smartphone, laptop, computer or tablet to another network where your IP address is hidden and all the data you generate while surfing the web is encrypted.
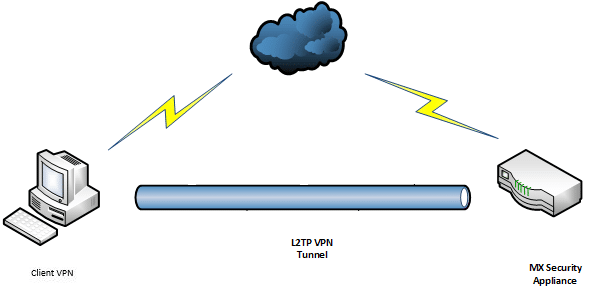
By connecting to websites via a VPN tunnel and not directly, you can help prevent businesses, government agencies, hackers, or other snoopers from tracking your online activity or viewing your Ipaddress which, like your actual address, identifies your location when you are online.
VPN History
The origins of VPNs can be traced back to Microsoft in 1996, when employees created a point-to-point tunneling protocol, also known as the peer-to-peer tunneling protocol or PPTN. This protocol is a method of creating a secure network between users through data encryption and forming a tunnel through a LAN or WAN connection.
This protocol makes the transfer of critical data safe and secure, even over public networks. All that is required to send data via PPTN is a username, password, and server address. Because of this, it remains one of the more popular and easy-to-use VPNs.
Understanding VPN
As a private connection, VPN is very important for personal needs or even for business needs, VPN is very important.
What is a VPN?
A virtual private network, or VPN, is an encrypted connection over the Internet from a device to a network. An encrypted connection helps ensure that sensitive data is transmitted securely. This prevents unauthorized persons from eavesdropping on traffic and allows users to perform work remotely. VPN technology is widely used in corporate environments.
How do VPNs Work?
In simple terms, the way a VPN works is to extend a corporate network through an encrypted connection made over the Internet. Since the traffic is encrypted between the device and the network, the traffic remains private throughout the journey. An employee can work outside the office and stay securely connected to the company network. Even smartphones and tablets can connect via VPN.
What Can a VPN Do?
The discussion above is the basics of VPN. The following are reasons why you should consider using a VPN. And what a VPN can do.
Remote Access
Many companies implement VPN services that allow employees and workers to access files, applications, printers, hard drives and other power sources in the office easily and certainly safe because VPNs have special paths on public networks.
Online Privacy and Security
Using a VPN is also an online privacy and security. It can be used to secure from public hotspots, security from ISPs, security from apps and services used, and also to avoid government regulations from the prohibited internet.
Geo Blocked Content
As mentioned earlier, VPNs can avoid government regulations from banned websites.
Even though many ISPs, applications, and internet data centers advise against selling your browsing data to the government, the information still finds its way into their hands. If you have doubts about government outreach, a VPN is a good investment to protect your data.
VPN Application Example
VPN services are available free of charge or paid. The provider’s application can be used for various devices by operating Windows, iOS, to Android. Usually, the basic VPN functions are available free of charge, but more complex features are found in paid VPN services.
Here are some of the most used and recommended VPN apps this year.
- NordVPN
- ExpressVPN
- VyprVPN
- CyberGhost
- IPVanish
- Surfshark
- Private Internet Access (PIA)
Various Tunneling Technologies
The technology of tunneling is indeed different. Not just a VPN, this tunneling consists of various technologies.
Proxy
The proxy server acts as a gateway between you and the internet. The proxy server acts as a firewall and web filter, provides a shared network connection, and stores data to speed up common requests. A good proxy server keeps users and internal networks protected from the bad things that live on the wider and wilder internet.
Anonymous Proxy
This is a server that functions as a relay between the user and the destination website. It hides the IP address of the user’s machine from the website and can provide encryption on the user’s side. Many organizations create their own anonymous proxy servers, and there are public access anonymous proxy servers on the Internet that anyone can use.
Traditional Proxy Server
Whereas traditional proxy servers allow multiple clients to route traffic to external networks. For example, a business might have a proxy that redirects and filters employee traffic to the public Internet. In contrast, reverse proxies route traffic on behalf of multiple
SSH Tunnel
SSH tunneling, or SSH port forwarding, is a method of transporting arbitrary data over an encrypted SSH connection. SSH tunnels allow connections made to local ports (that is, to ports on your own desktop) to be forwarded to remote machines over a secure channel.
To protect our network services, not all of them can be reached directly from outside the network. If you are out of location and need to access the protected resource in this way, you can use ssh to browse the accessible resource to reach the protected resource.
VPN
While the last one is a VPN. This technology creates a fake point-to-point connection that can be used immediately to send and receive data. However, in VPN technology, tunnels are not allowed like that without being given an additional security system. The tunnel is equipped with an encryption system to protect the data that passes through the tunnel. It is this encryption work that makes VPN technology secure and private.
Benefits of Using a VPN
The following are the benefits that you can really get when you use a VPN to access the internet by using a VPN. Although this VPN is considered a technology that can open various websites that are blocked by the government and do so illegally, the fact is that VPNs were not only born and created for this.
There are still many benefits of using a VPN, including:
Securing Data Communication When Using Public / Public Wifi Networks
Websites and apps can continuously track your online activities, analyzing the data they collect. A VPN can prevent web browsers and other people from accessing your connection, especially when you are using a public wifi connection which is very vulnerable to data theft. A VPN helps keep the information you send and receive anonymous and secure. Some VPNs also offer military-grade 256-bit encryption for your data.
Accessing the Office Network from Anywhere Using the Internet
VPN can help employees who are working at home to be able to access the office network anywhere and anytime using the internet. This VPN is very helpful for network security.
For companies that need a certain secure network, then a VPN is an ideal solution at a low cost.
By using a VPN, the company’s mobility level will run better, where employees can consistently connect to the office network using personal devices at home.
Creating Inter-Branch Network at Low Cost
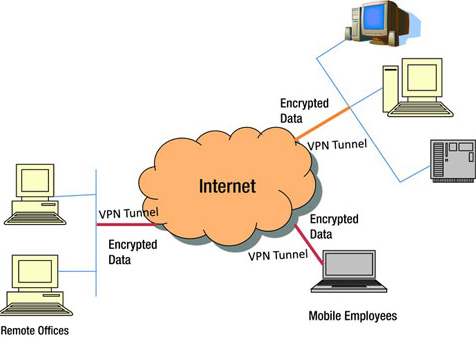
VPN can be used as an interconnection between branch office connections. VPN can also be able to connect thousands of devices (VPN clients) simultaneously without problems such as overload or intermittent connections. But you need to make sure that the internet connection at your server/store/branch location has a decent enough bandwidth for the large amount of data that passes through.
Bypass Firewall (Bypass Blocking)
VPNs don’t break through firewalls much when they tunnel through a tunneling protocol. Almost all VPNs have a tunneling protocol that hides your traffic, giving you perfect anonymity and security when browsing the web.
Reducing Latency or Lag in Online Games
For lag problems when you play online games caused by bad routing, it can be solved by applying a VPN or tunnel to a server that has better routing tracks.
Netdata warns, a VPN will only solve lag problems due to bad routing, not lag because wifi is used a lot.
![]()