Cyber attacks, maybe there will be no end to discussing this because in reality there are so many crimes in cyberspace that threaten us. One of the cyber attacks that is considered dangerous is the botnet. Have you ever heard of it? Maybe this is still very foreign to most people.
Before reading further, for those of you who want to know more about Netdata, you can contact us directly via the link below.
Therefore, because this cyber attack is considered very dangerous, it is better for you to know what a botnet is, the impact that occurs if you are hit by a botnet, how it works, and how to avoid botnets.
Table of Contents
What are Botnets?
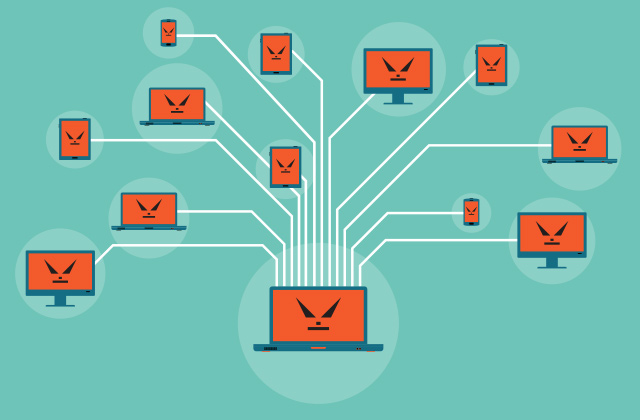
A robot network, or what people usually call a botnet, is a network of computers infected with malware that is under the control of one attacker, known as a “bot-herder.” Each individual machine under the control of a bot-herder is known as a bot. From a single central point, an attacker can command every computer in the botnet to simultaneously commit coordinated criminal acts.
The scale of botnets (many consisting of millions of bots) allows attackers to perform large-scale actions that were previously impossible with malware.
Because it remains under the control of a remote attacker, an infected machine can receive updates and change its behavior on the fly. As a result, bot-herders are often able to rent access to segments of their botnets on the black market to make significant financial gains.
How Botnets Work
Botnets are created when bot herders send bots from their command and control servers to unknown recipients using file sharing protocols, email, or other social media applications or bots as intermediaries. Once the recipient opens the malicious file on their computer, the bot reports back to command and control where the bot’s herdsman can dictate commands to the infected computer. Below is a diagram illustrating this relationship:
A number of unique functional features of bots and botnets make them suitable for long-term disruption. Bots can be updated by the bot herder to change all of their functions based on what he wants them to do and to adapt to changes and countermeasures by the target system.
This highlights that infection is the most critical step, as functionality and communication methods can always be changed later as needed.
Types of Botnet Attacks
Botnet attacks can be grouped into 3 types, including:
Phishing
This attack is usually carried out via email. Although email is seen today as an older attack vector, spam botnets are some of the largest in size. They are primarily used to send spam messages, often including malware, to large numbers of bots. The Cutwail botnet, for example, can send up to 74 billion messages per day. They are also used to deploy bots to recruit more computers to the botnet.
DDoS Attacks
DDoS attacks take advantage of the large scale of botnets to overload the target network or server with requests, making them inaccessible to the intended users. DDoS attack target organizations for personal or political motives or to extort payment in return for stopping the attack.
Brute Force Attack
The latter is a brute force attack. Brute force attack is a trial and error method used to decode sensitive data. The most common applications of brute force attacks are cracking passwords and cracking encryption keys (keep reading to learn more about encryption keys).
Other common targets for brute force attacks are API keys and SSH logins. Brute force password attacks are often carried out by scripts or bots that target the login page of a website.
Impact of Botnet Attacks
The impact of attacks from this botnet is indeed very detrimental. Even the device that you use if it has been hit by a botnet will be like a zombie.
As discussed, zombie tools often called bots can be termed as devices that have been taken over by bot herders as part of a botnet, mainly due to malware infections. These devices, once compromised, will blindly follow the C&C server’s commands.
How To Avoid Botnets
Because that’s how dangerous an attack from a botnet is, how can you avoid a botnet? The following is the most appropriate way:
Update Admin Settings and Passwords on All Devices
Your team should regularly update your OS, applications, passwords and software solutions. Ideally as soon as an update is available. Security patches are there for a reason, and most software vendors will publish known vulnerabilities soon after they are patched. If you haven’t updated your OS when the vulnerability was discovered by hackers, now it may be a potential gateway for bot herders to infect your system and recruit them into the botnet.
If you cannot set up automatic software and firmware updates on all your systems and devices for any reason, schedule regular manual updates at least once a week.
Avoid Using Devices With Less Security
A very possible way is for you to avoid using devices that lack security. If you are still using a device that still has insufficient security and you store various kinds of data there, it is very possible that this botnet will attack your device.
Be careful opening email attachments
Avoid downloading email attachments unless you are 100% sure of the identity of the sender. Investigate and verify the sender’s email address carefully before clicking on an unexpected attachment or link.
Don’t click random links
Avoid clicking any link in any message (email, text message, social media direct message, etc.) unless you are 100% sure about the sender. When you need to visit a link, it’s better to manually enter the URL into your browser’s address bar to avoid DNS cache poisoning, rather than clicking.
Use Strong Passwords
Always use strong or complex passwords for all your accounts, including admin accounts on all devices connected to other devices or directly to the internet. Also, make sure each password is unique for only one account.
Install the Best Antivirus
Since most conversions occur due to malware infections, it is very important to invest in a sufficiently powerful antivirus/anti-malware software that can protect your devices and systems from botnet malware and other digital threats. Also, make sure to update your antivirus solution regularly.
Conclusion
Botnets are indeed one of the cyber attacks that are considered very dangerous. Make this a serious matter and need to be discussed for the survival of your business rather than getting yourself hit by a botnet.
While botnet attacks can be difficult to defend against, they are not impossible. By taking precautions as above, it is guaranteed not to attack your device.
NetData is a company that provides technology-based services with the best service and quality, if you are interested in us you can contact us directly via this link or via our contact form here.
![]()