The Mikrotik configuration does have a lot of features and advantages that are very much in demand by network users.
Field facts in the Mikrotik configuration sometimes an error occurs which can make Mikrotik function not optimal. Now at this time we will discuss about the Troubleshooting of the most common Mikrotik Configurations.
Access Port Not Closed
The first is the unclosed access port error on Mikrotik. Basically, the Mikrotik configuration provides a strong enough password, but if the access port is not closed, it will be very prone to Brute Force.
What is Brute Force? Brute Force is a persistent login attempt attack using the method of trying all password combinations in sequence.
Then how do I close this access port? Here are the steps:
First we create a Winbox application
Then select menu IP> Service.
In some of the service lists below, we can disable any port access that we don’t need by selecting a service then clicking the X on the menu above the window.
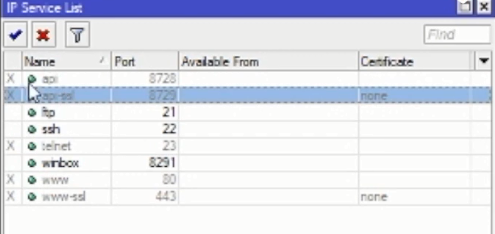
Or want to be more advanced, we can choose a port that we want to access privately via our local IP as below.
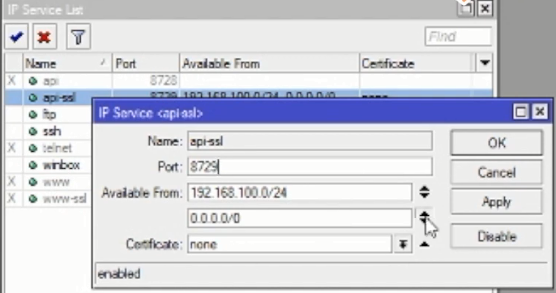
Table of Contents
Unsafe Mikrotik Configuration
DNS Servers or Proxy Servers inDNS Servers or Proxy Servers that are not on this firewall are prone to being scanned by someone to find which ports are open. So that you can entrust traffic to the Mikrotik router.
This is common in middle to lower class companies, if usually in the ISP class, what is needed is already determined so that it will not happen.
Some may think that it’s okay not to take up a lot of bandwidth. Now the problem is if there is a DNS amplification attack which can eat up hundreds of MB of bandwidth.
Then how do I fix it? The trick is to simply set up the Firewall in the following way:
Go to the IP> Firewall menu.
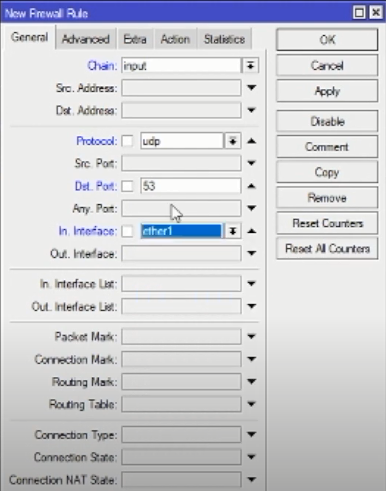
Create a rule newon the general tab.
- Chain: Input.
- Protocol: udp.
- Port: 53
- Interface: ether1
On the Action tab:
- Action: drop then Apply
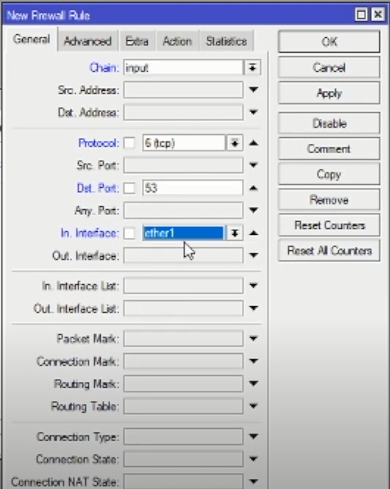
Then create a rule new again.
The method is the same as before but in the protocol: tcp.
Action Drop
Create rules again with the TCP protocol and so on. Port: 8080
And Action: Drop.
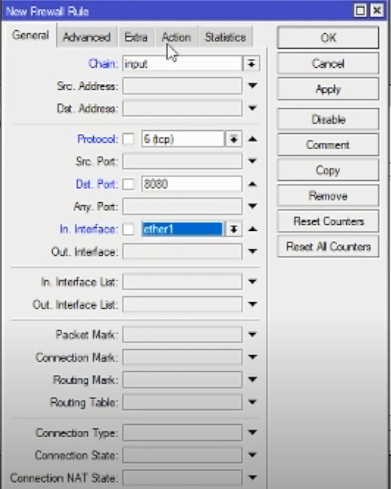
Load Balancers that do not use special rules
On load balancers that do not use specific rules for routing, the data packet will experience confusion.
This data packet confusion, for example, when incoming data from ISP1 can go out to ISP2 or vice versa, it can cause packets to collide.
Now the solution we have to make a special rule in the following way:
Download Firewall
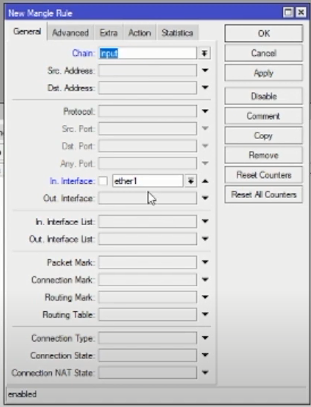
Open themenu IP > Firewall > Tab Mangle > + create a rule here.
- Fill Chain: input
- interface: ether1
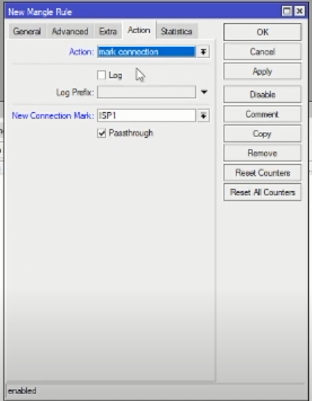
On the Action tab:
- Action: mark connection
- New connection mark: ISP1
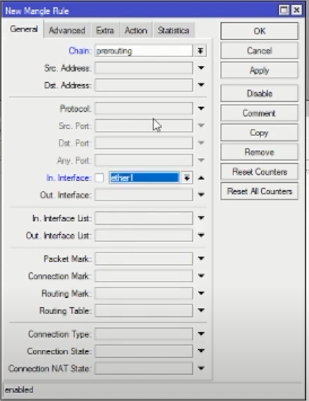
Then create a new rule again:
- Chain: prerouting
- interface: ether1
On the tab it is Action still the same, mark the connection then Apply.
Firewall Upload
new rule with parameters:
- Chain: prerouting
- interface: ether1
- Connection mark: ISP1
Tab Action: connection mark
New connection mark: ISP1
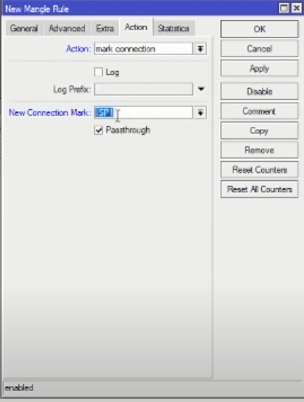
Create a routing mark by creating a new rule with parameters:
- Chain: Output
- Connection mark: ISP1
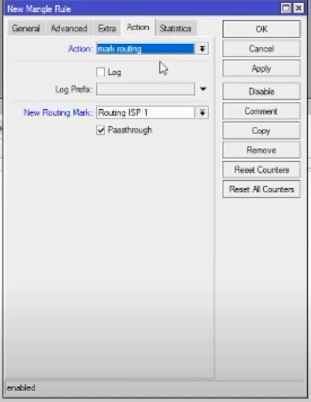
Tab action:
- Action: mark routing.
- New connection mark: Routing ISP 1
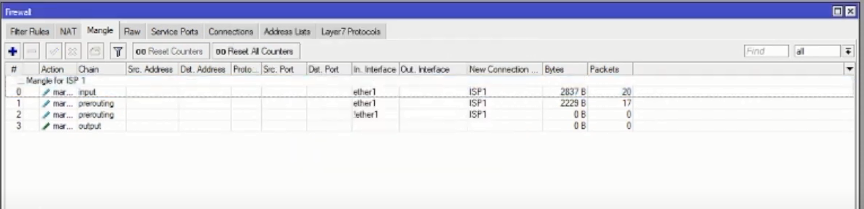
If you have, then you have 4 new rules as below:
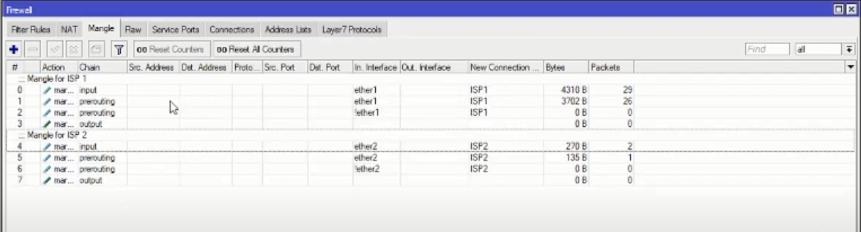
For ISP2, we also need to create new rules specifically for ISP2. The method is the same as creating ISP1 but in the action tab the new connection mark : ISP2.
So you will have 8 new rules as below:
At this point the Firewall creation is complete, now the next step is to set the Route by means of IP > Routes.
Create a new route by pressing the “+” then fill in the parameters as below:
ISP1:
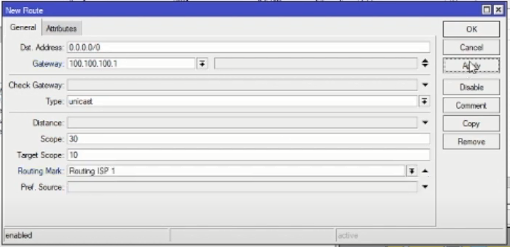
ISP2:

Until here it is finished.
That’s some troubleshooting about Mikrotik problems that often occur and how to handle them.
If you are still confused about Mikrotik problems you can ask directly on the official NetData Instagram @ NETDATA.ID or send an email to sales@nds.id. Interested in the proxy configuration service from NetData? You can contact us here.
Troubleshooting and Errors – Errors in Mikrotik Configuration | Netdata IT Tutorials
![]()


